Check Point research has reported that email-based phishing attacks saw the highest increase in number, compared to any other platform in Q2. The most common of these emails are impersonation emails asking users to reset or submit their Microsoft account credentials, in order to gain control over their accounts. In the third quarter of 2020, email was the most used platform for impersonation attacks, accounting for a staggering 44% of the attacks total, with Microsoft being the most imitated brand for impersonation phishing attempts (19% of total), followed by Google (9% of total).
The attacks will often look like the example below:
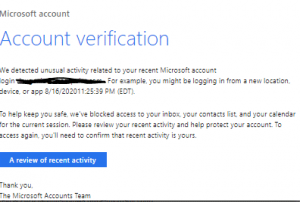
The increase in phishing emails in Q3 of 2020 is one of the most prominent trends of the Work-From-Home era. Cyber criminals are well aware of the distractions people are dealing with while trying to work and be productive from home. Combined with the enormous amount of emails employees receive every day, the recipe for a successful email phishing campaign is complete. Worse is that an email phishing attack is often the first step in a multi-staged attack that puts your entire organization at risk. When cybercriminals obtain one employee’s account credentials, they have access to corporate data, and can use the hijacked account to send further phishing emails to other employees in the organization, pretending to be the hijacked account’s owner. These attacks can results in huge costs, loss of sensitive data and even compliance fines, in case of a customer data breach.
What to do?
Again, ensure your staff is well informed of this phishing technique. Routinely scheduled security briefs are recommended.
You must consider a solution that provides complete protection from all attacks for both email and productivity suite applications such as Teams, OneDrive, Google Drive and others
What can you do to when this happens to you?
If you think your network security has been breached shut the network down and identify any malware/viruses / or data exfiltration. Mitigate the breach and notify affected users/organizations. Reinstate the network using a known “clean” backup.
Sources.
Microsoft & Google Impersonation Attacks Are on the Rise – How to Stay Safe – Check Point Software
