Zoom email scam” refers to an email spam campaign. The term “spam campaign” is used to describe a mass-scale operation, during which thousands of deceptive emails are sent. The letters, distributed through this spam campaign, claim recipients have received a video conferencing invitation on the Zoom (Zoom Video Communications, Inc.) videotelephony and online chat service platform. It must be emphasized that these scam emails are in no way associated with the actual Zoom service. The letters are used to promote a phishing website, which is designed to record information entered into it.
An example is shown below
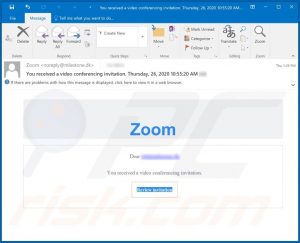
The title/subject of these scam emails – “You received a video conferencing invitation” – contains the essence of the letters. The body of the letters simply greets the email recipient and informs them that they have been invited to a Zoom video conference. However, when the “Review invitation” button is clicked – recipients are redirected to a phishing webpage. This page requests users to sign-in using their Microsoft accounts. Instead of accessing the fake Zoom conference invite – users unintentionally expose their Microsoft account log-in credentials (i.e. usernames and passwords) to the scammers behind this spam campaign. Commonly, information of interest includes (but is not limited to): names, surnames, addresses, telephone numbers, email addresses, banking account and/or credit card details. Furthermore, phishing may be used in tandem with other scams.
Systems are infected through virulent files, which are distributed via spam campaigns. The files can be attached to the deceptive emails and/or the letters contain download links of such content. Infectious files can be in various formats, e.g. archives (RAR, ZIP, etc.), executable (.exe, .run, etc.), PDF and Microsoft Office documents, JavaScript, and so on.
What to do?
Do not open suspicious and irrelevant emails, especially any attachments or links found in them – as that can result in a high-risk system infection
Use Microsoft Office versions released after 2010.
Use official/trustworthy download sources, as well as activate and update programs with tools/functions provided by legitimate providers.
Have a dependable anti-virus/anti-spyware suite installed and kept updated. This software has to be used for regular system scans and removal of detected/potential threats
What can you do to when this happens to you?
If you’ve already opened malicious attachments, we recommend running a scan with a reliable antivirus / malware detection software to automatically eliminate infiltrated malware.
Sources.
How to remove Zoom Email Scam – virus removal guide (pcrisk.com)
